Environment variables and configuration volumes
Environment Variables
Add the environment variables here. These will be available to the container at runtime.
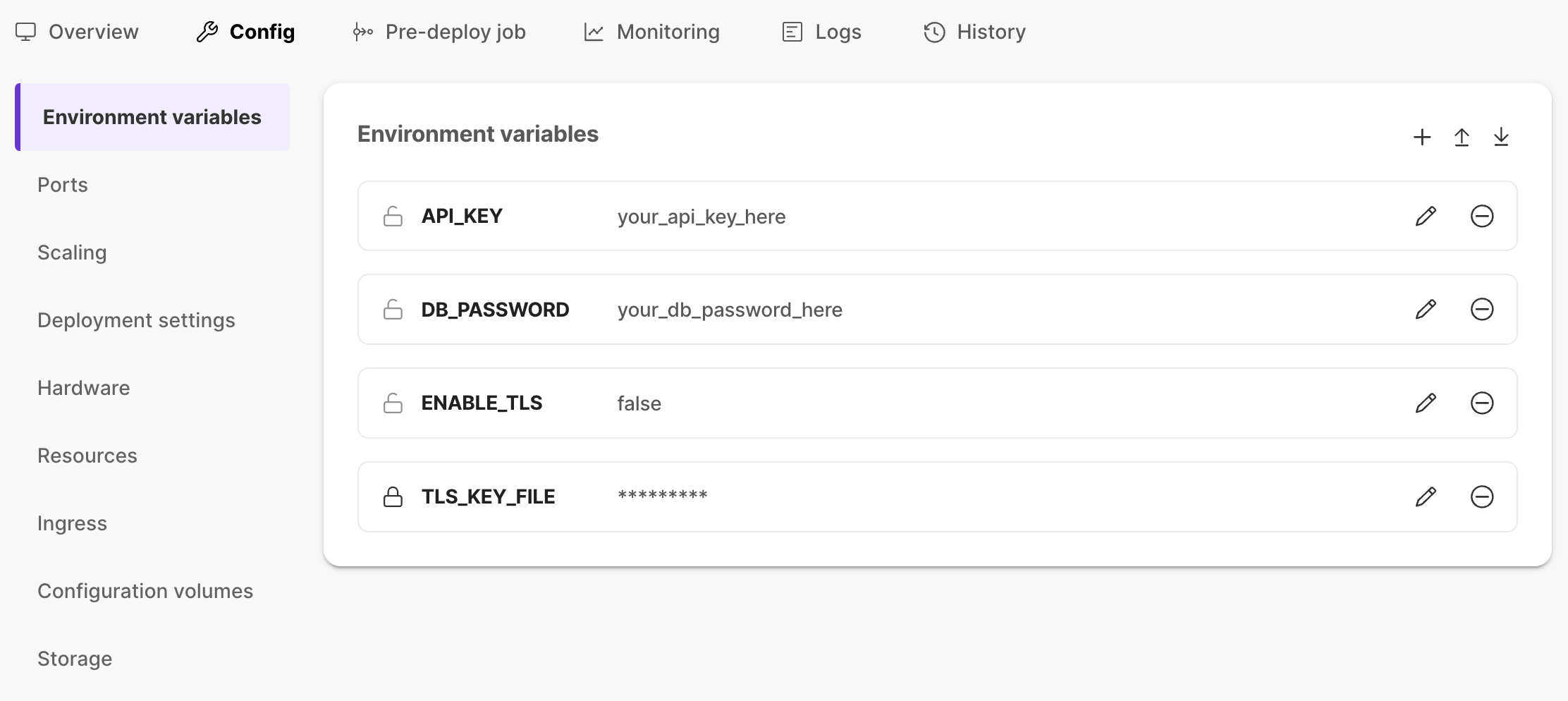
You can mark the value as a secret by clicking the "Lock" icon, see secret management for more information.
Upload .env file:
- You can add multiple environment variables by uploading a ".env" file.
- Shared variables can be added using
${env.<VARIABLE_NAME>}in values. - The file should be in the format of key-value pairs. E.g.,
DB_HOST=localhost
DB_PORT=3306
DB_USER=${env.DB_USER}
Download .env file:
You can download all of your environment variables (key-value pair) by clicking on the download icon at the top right corner. Note that secret values will not be downloaded. Shared environment variables will be downloaded with the format ${env.<VARIABLE_NAME>} in values.
Value of environment variable is not interpreted or decoded.
For example, if value of a variable is set to first line\nsecond line then container will see value of variable as
first line\nsecond line,- and not
first line
second line
For values that contain escape sequences, it is recommended to use configuration volumes.
Configuration volumes
Configuration volumes are used to define variables, similar to environment variables. These are recommended to store large multiline textual values. Typically, volumes are used for SSL certs, private keys, or tokens. You can have multiple volumes per container. The path of the volume becomes the key, and file content becomes the value of the variable. A volume has the following configuration variables:
- Config File: First upload the configuration (value) file.
- Stored as a secret: Tick this if you like your volume to be stored as a secret in your cloud provider's secret store, see secret management for more information.
- Hardcoded Path: Provide a path to the volume. E.g.,
/temp/config - Name of the Volume: A meaningful name to identify the volume.
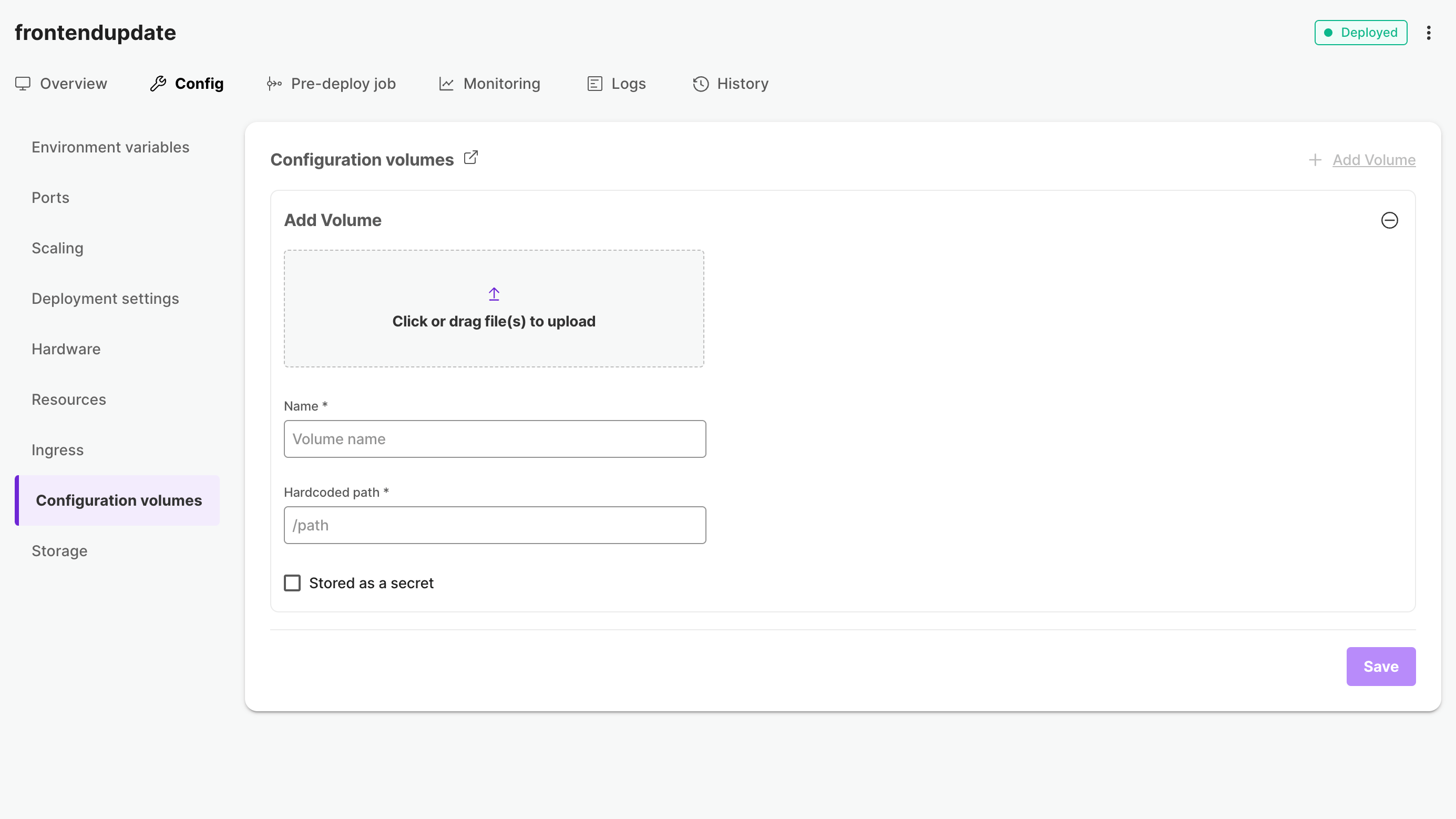
To create a configuration volume, go to Configuration volumes sub-tab under Config tab of an application, upload a configuration file and fill in the details. Click on "Save" to create the volume.
When accessing value stored in configuration volume, it has to be read as a file. To simplify reading values from both configuration volumes and environment variables, we recommend using following approach in application code.
- JavaScript
- Python
- Java
- Go
if (fs.existsSync(envVarName)) {
value = fs.readFileSync(envVarName, 'utf8').trim();
} else {
value = process.env[envVarName];
}
if os.path.exists(env_var_name):
with open(env_var_name, 'r') as file:
value = file.read().strip()
else:
value = os.getenv(env_var_name)
File file = new File(envVarName);
if (file.exists()) {
try {
value = new String(Files.readAllBytes(file.toPath())).trim();
} catch (IOException e) {
value = System.getenv(envVarName);
}
} else {
value = System.getenv(envVarName);
}
if _, err := os.Stat(envVarName); err == nil {
content, err := ioutil.ReadFile(envVarName)
if err != nil {
value = os.Getenv(envVarName)
} else {
value = string(content)
}
} else {
value = os.Getenv(envVarName)
}
Secret Management
Secret values are stored in your cloud provider's secret store and written directly to your cluster during service deployment by External Secrets Operator. This means the value will never be saved or cached in Kapstan and will not be read by Kapstan at any point after the initial save.
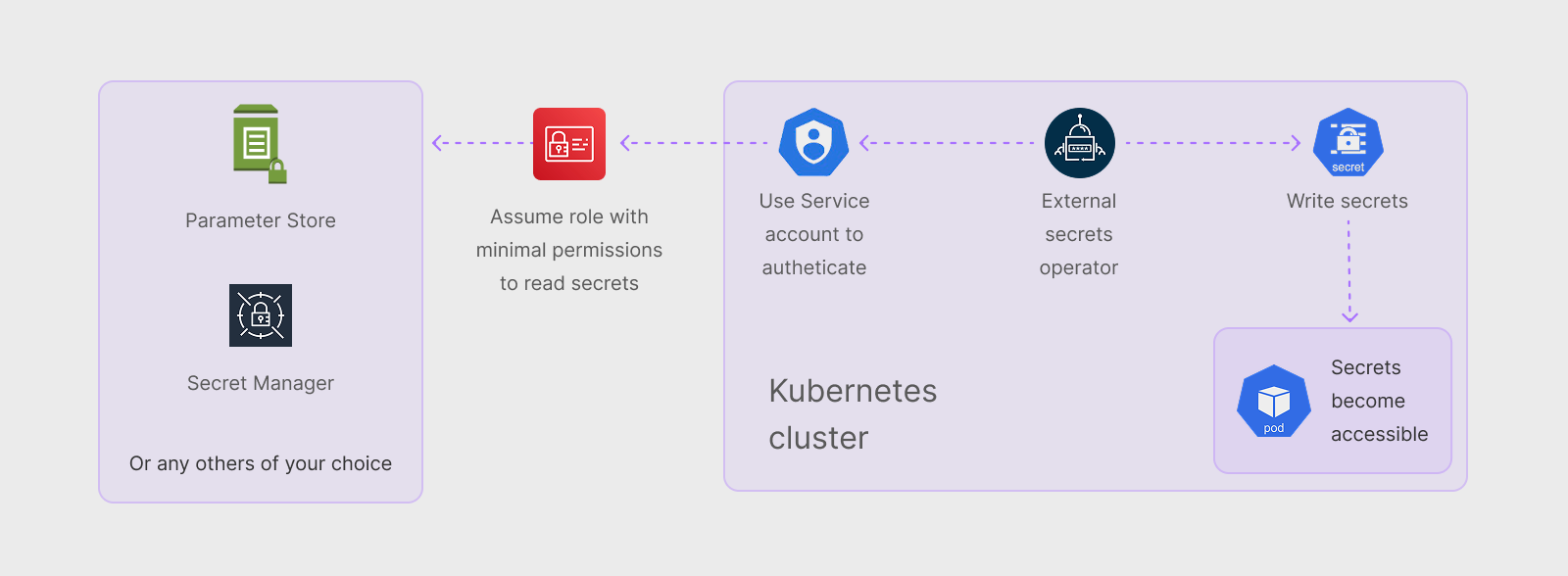
To mark an environment variable or configuration volume as a secret, click the "Lock" icon. This will store the value in your cloud provider's secret store.

